Chapter 12 - Safety engineering
Chapter 13 - Security engineering
# Quiz
Safety-critical systems are systems whose failure can lead to human injury or death.
Static analysis is an approach to V & V that examines the source code (or other representation) of a system, looking for errors and anomalies. It allows all parts of a program to be checked, not just those parts that are exercised by system tests.
What are the two classes of Safety-critical software
Which of the following are potential system accidents that may ocurr
Match the Fault Class with the Status Analysis Checks
- Data faults
Variables used before initialization Variables declared but never used Variables assigned twice but never used between assignments Possible array bound violations Undeclared variables
- Control faults
Unreachable code Unconditional branches into loops
- Input/output faults
Variables output twice with no intervening assignment
- Interface faults
Parameter type mismatches Parameter number mismatches Nonusage of the results of functions Uncalled functions and procedures
- Storage management faults
Unassigned pointers Pointer arithmetic Memory leaks
- Data faults
The three security dimensions are Confidentiality, Intelligence, and Accessability
Security is a system attribute that reflects the ability of the system to protect itself from malicious internal or external attacks.
In most cases, it is trivial to add security to a system after it has been implemented. Thereforce, security issues can be taken into account after the system design process.
Security design guidelines sensitize system designers to security issues that they may not have considered. They provide a basis for creating security review checklists.
# Exercise
Identify six consumer products that are likely to be controlled by safety-critical software systems. Explain your reasoning for each.
In the safety-critical systems, the system operation is always safe. These systems ensure safety to the people. The system should never damage people or its environment. Some of the safety-critical systems are automobile control systems, monitoring systems in aircraft etc.
- Following are the six consumer products that are likely to be controlled by safety-critical systems
- Vacuum cleaner - Incorrect operation may cause serious injury to users or people around them
- Blender - Incorrect operation may cause serious injury to users or people around them
- Microwave oven - Improper use may lead to explosion and fire
- Electric drilling machine or electrical saw - Incorrect operation may cause serious injury to users or people around them
- Garbage disposal unit - Incorrect operation may cause serious injury to users or people around them
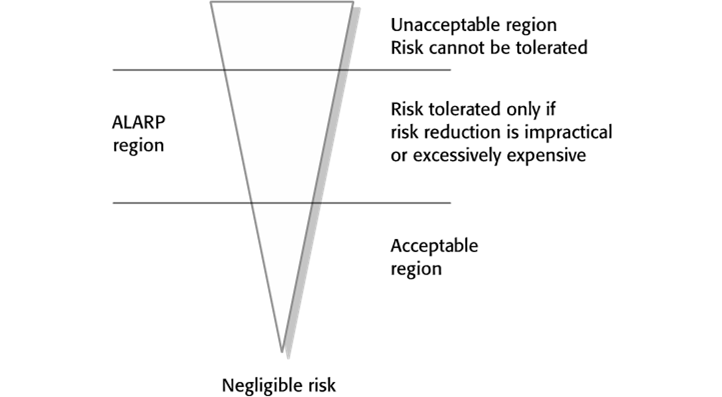
A software system is to be deployed for a company that has extremely high safety standards and allows for almost no risks, not even minor injuries. How will this affect the look of the risk triangle in Figure 12.3 in the textbook?
Risks may be categorised as:
Intolerable: Must never arise or result in an accident
As low as reasonably practical(ALARP): Must minimise the possibility of risk given cost and schedule constraints
Acceptable: The consequences of the risk are acceptable and no extra costs should be incurred to reduce hazard probability.![]()
The width of the triangle reflects the cost of ensuring that the risk does not lead to accidents. If no risk is allowed, there will be a cost for any risk. The hazard triangle may appear as a rectangle.Explain when it may be cost-effective to use formal specification and verification in the development of safety-critical software systems. Why do you think that some critical systems engineers are against the use of formal methods?
Formal specifications are very effective in discovering those specification problems that are the most common causes of system failure. Formal verification is impractical for large systems, but it can be used to verify critical-safety and security-critical components.
Verifying large software systems takes a much time and requires mathematical expertise and specialized software tools. It is therefore an expensive process and, as the system size increases, the costs of formal verification increase disproportionately. Therefore many software engineers think that the formal verification is not cost effective. They believe that the same level of confidence can be achieved more cheaply by using other validation techniques, such as inspections and system testing.
List four types of systems that may require software safety cases, explaining why safety cases are required.
A safety case is a set of structured documents that includes a description of the system to be certified. It contains the information about the processes used to develop the system and logical arguments that demonstrate that the system is safe or that a required level of security is achieved. Therefore, for many critical systems the safety case is a legal requirement. Software failures can result in failures of equipment or other processes which may lead to injury or death. Safety cases may vary depending on the type of the system.
The systems that may require safety cases are:
- Banking system
- Nuclear power system
- Health care system
- Air-traffic control systems
The door lock control mechanism in a nuclear waste storage facility is designed for safe operation. It ensures that entry to the storeroom is only permitted when radiation shields are in place or when the radiation level in the room falls below some given value (dangerLevel).
- So,
i. If remotely controlled radiation shields are in place within a room, an authorized operator may open the door.
ii. If the radiation level in a room is below a specified value, an authorized operator may open the door.
iii. An authorized operator is identified by the input of an authorized door entry code. - The code shown below controls the door-locking mechanism. Note that the safe state is that entry should not be permitted. Using the approach discussed in this chapter, develop a safety argument for this code. Use the line numbers to refer to specific statements. If you find that the code is unsafe, suggest how it should be modified to make it safe.
![]()
- Code above as a text box for editing
entryCode = lock.getEntryCode () ; if (entryCode == lock.authorizedCode) { shieldStatus = Shield.getStatus(); radiationLevel = RadSensor.get(); if (radiationLevel < dangerLevel) { state = safe; } else { state = unsafe } if (shieldStatus == Shield.inPlace()) { state = safe; } if (state == safe) { Door.locked = false ; Door.unlock(); } else { Door.lock(); Door.locked := true ; } }
There are two potential safety problems with this code:
Say the door was unlocked when the door entry code was entered. Line 13 checks if the state is safe and, if it is safe then unlocks the door. However, if the door was unlocked to begin with, there is no locking action if the state is unsafe so therefore a potential safety loop hole exists.
If the radiation level is less than the danger level then line 8 sets the state to be safe. However, line 10 checks the shields to see if they are in place. If they are not in place, the state is unchanged although, in fact, the system is unsafe if the shields are down. Therefore, the door can be opened with the shields down and a safety loophole exists.
There are two changes which should be made to ensure that the code is safe:
- An initial statement which locks the door and sets door locked to be true.
- The if statement if shield-status == Shield.inPlace then should be changed to:
if (shield_status == Shield.inPlace()) { state := safe; } else { state := unsafe; }There are other ways to do this with nested if statements.
- So,
Describe the security dimensions and security levels that have to be considered in secure systems engineering.
Security dimensions:
Confidentiality: Information in a system may be disclosed or made accessible to people or programs that are not authorized to have access to that information.
Integrity: Information in a system may be damaged or corrupted making it unusual or unreliable.
Availability: Access to a system or its data that is normally available may not be possible.Security levels:
Infrastructure security, which is concerned with maintaining the security of all systems and networks that provide an infrastructure and a set of shared services to the organization.
Application security, which is concerned with the security of individual application systems or related groups of systems.
Operational security, which is concerned with the secure operation and use of the organization’s systems.Explain why security is considered a more challenging problem than safety in a system.
Security: Protection of a system against deliberate external attacks and threats.
Safety: Protection of the users of a system from unintended risks.
The key difference here is that while security is protection from external attacks, safety is almost purely an internal affair. It is clear that security being mostly external in nature has a broader coverage.
Safety cannot be achieved if security is not guaranteed.
This is what makes it more challenging than safety.Explain why it is important to log user actions in the development of secure systems.
Maintain a log of user actions that can be analyzed to discover who did what. If users know about such a log, they are less likely to behave in an irresponsible way.
Explain why it is important when writing secure systems to validate all user inputs to check that these have the expected format.
When writing secure systems, it is important that all user inputs are validated against expected format. This validation is necessary to ensure that all exceptions are handled correctly and that unexpected inputs do not cause the system to crash. In secure system, it is therefore important to validate user inputs to prevent malicious users from exploiting the system.
Suggest how you would go about validating a password protection system for an application that you have developed. Explain the function of any tools that you think may be useful.
Verification and validation process for a password protection system must focus on security assessment. Validating a password protected system may include:
- Check for the password set to system is strong password which may consist of mixed alphanumeric characters and punctuation which are difficult to break.
- Password length should be of maximum size and is not same as the user name.
- Sessions should end after a period of inactivity and sessions should be ended at the time of logout.
- Never use cookies for storing passwords. Use hashed passwords to store in a database like SQL to avoid SQL poisoning attack.
- The files used in the application should have appropriate access permissions to avoid unauthorized access of the file.